In an evaluation of smartphones from 10 producers, researchers at TU Graz have discovered that the Android kernels used are susceptible to identified assaults—so-called one-day exploits—regardless of present safety mechanisms.
Smartphones are a relentless companion and necessary work device for many individuals. Along with contacts, appointments and emails, the units are more and more getting used for delicate duties resembling on-line banking or official issues. This will increase the security necessities.
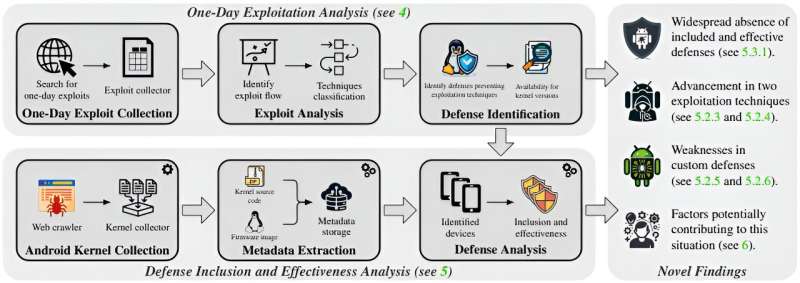
As Lukas Maar, Florian Draschbacher, Lukas Lamster and Stefan Mangard from the Institute of Utilized Data Processing and Communications at Graz College of Know-how (TU Graz) have found in a complete evaluation of the Android kernels of the ten largest and most well-known smartphone producers, there are quite a few flaws right here that enable one-day exploits utilizing already identified assault strategies. The researchers introduced their findings on 15 August on the Usenix Safety Symposium in Philadelphia.
Relying on the producer and mannequin, solely between 29% and 55% of the 994 smartphones examined by the analysis group had been in a position to forestall assaults. In distinction, the Generic Kernel Picture (GKI) model 6.1 supplied by Google would have the ability to forestall round 85% of assaults.
In comparison with the GKI, the producer kernels carried out as much as 4.6 instances worse in defending towards assaults. The analysis group analyzed units from these producers that got here onto the market between 2018 and 2023 (itemizing from probably the most safe to the least safe): Google, Realme, OnePlus, Xiaomi, Vivo, Samsung, Motorola, Huawei, Oppo and Fairphone.
The Android variations used on these smartphones ranged from variations 9 to 14, whereas the kernels lined the vary from variations 3.10 to six.1, with producers who depend on decrease kernel variations additionally providing much less safety.
Efficient protection mechanisms not often activated
One other key level of the evaluation is that there are already efficient defenses for a lot of the identified assault strategies, however they’re both not often activated within the producers’ kernels or the kernels are configured incorrectly. Because of this, even kernel model 3.1 from 2014 with all safety measures activated might present higher safety towards identified assaults than about 38% of the kernels configured by the producers themselves.
The researchers additionally discovered that producers’ low-end fashions had been about 24% extra in danger than high-end fashions. One necessary purpose for that is the lack of efficiency that extra safety measures could cause, which is why they’re typically deactivated in low-end fashions to preserve assets.
“We hope that our outcomes will assist to make sure that simpler safety measures could be present in producers’ kernels sooner or later, making Android safer,” says Maar. “We additionally shared our evaluation with the producers investigated and Google, Fairphone, Motorola, Huawei and Samsung have taken be aware—some have even launched patches.
“We’ve additionally urged that Google replace the Android Compatibility Definition Doc (CDD), which units out the framework of necessities for units to be appropriate with Android.
“Google itself has emphasised that it’s conscious of the issue and desires to strengthen the combination of kernel safety measures step-by-step. Nevertheless, it’s as much as the producers whether or not they need to sacrifice efficiency for this.”
Extra data:
Defects-in-Depth: Analyzing the Integration of Efficient Defenses towards One-Day Exploits in Android Kernels. www.usenix.org/convention/usen … ntation/maar-defects
Quotation:
Quite a few producers use insecure Android kernels, evaluation reveals (2024, August 16)
retrieved 16 August 2024
from https://techxplore.com/information/2024-08-numerous-insecure-android-kernels-analysis.html
This doc is topic to copyright. Other than any truthful dealing for the aim of personal research or analysis, no
half could also be reproduced with out the written permission. The content material is supplied for data functions solely.



