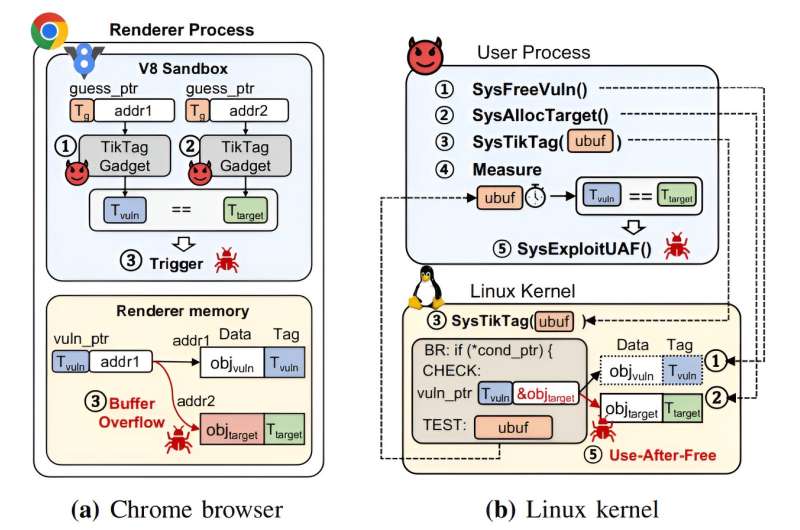
A mixed staff of safety specialists from Seoul Nationwide College and Samsung Analysis has discovered a vulnerability in reminiscence tagging extensions (MTEs) employed by ARM processors as a method of safety from reminiscence leaks. The group has revealed a paper describing their findings on the arXiv preprint server.
In 2018, Arm, Ltd., launched a brand new {hardware} function for superior diminished instruction set pc (RISC) machines (ARMs) that could possibly be utilized by software program makers to detect reminiscence violations. MTEs tag blocks of bodily reminiscence with metadata.
When software program makes a reminiscence name inside a tagged area, usually utilizing a pointer, the brand new {hardware} seems to see if the pointer holds an identical key for the referenced reminiscence block. If not, an error is returned, stopping knowledge from being written the place it’s not alleged to occur—akin to throughout buffer overflows.
The introduction of MTE has been thought-about a gorgeous addition to the ARM structure as a result of it helps programmers forestall reminiscence corruption and attainable vulnerabilities akin to hackers accessing knowledge in unsecured areas. Sadly, it seems that the introduction of MTEs has additionally led to the introduction of a brand new vulnerability.
On this new work, the analysis staff developed two methods they name TIKTAG-v1 and -v2 that they declare are able to extracting MTE tags for random reminiscence tackle areas. They clarify that each methods contain using software program to look at as speculative operations affect the best way that knowledge is pre-fetched.
Software program programs use pre-fetching to hurry up operations, stopping lag instances related to ready for knowledge retrieval. Speculative executions work in a lot the identical manner, executing code upfront that may be helpful at a future level, generally utilizing pre-fetched knowledge and writing to reminiscence. If the outcomes of such executions are usually not wanted, they’re merely discarded. The vulnerabilities the staff discovered concerned profiting from such pre-fetched and/or discarded data.
The analysis staff discovered that they have been capable of extract MTE tags in 95% of their makes an attempt, which, they be aware, may result in exploitation. In addition they proposed a number of attainable options to repair the issue, which they despatched to Arm, Ltd.
Extra data:
Juhee Kim et al, TikTag: Breaking ARM’s Reminiscence Tagging Extension with Speculative Execution, arXiv (2024). DOI: 10.48550/arxiv.2406.08719
© 2024 Science X Community
Quotation:
Safety specialists discover vulnerability in ARM’s reminiscence tagging extensions (2024, June 19)
retrieved 23 June 2024
from https://techxplore.com/information/2024-06-experts-vulnerability-arm-memory-tagging.html
This doc is topic to copyright. Other than any truthful dealing for the aim of personal research or analysis, no
half could also be reproduced with out the written permission. The content material is offered for data functions solely.



